Warning: Coronavirus Pandemic a Target Rich Environment for Fraudsters
Warning: Coronavirus Pandemic a Target Rich Environment for Fraudsters
THEFT AND FRAUD
This post is about our susceptibility to fraud in this time of crisis.
Much like theft, fraud involves illegally obtaining goods, services or money by false pretences. There is a close relationship between theft and fraud. According to the Criminal Code of Canada:
Every one commits theft who fraudulently and without colour of right takes, or fraudulently and without colour of right converts to his use or to the use of another person, anything, whether animate or inanimate, with intent (a) to deprive, temporarily or absolutely, the owner of it….
REAL VICTIMS, REAL CRIMINALS
As a criminal defence lawyer, I strongly believe in the right to a fair trial, the right to be presumed innocent until proven guilty and the right in Canada to receive the full protection of the Canadian Charter of Rights and Freedoms. Doubtless, most Calgary criminal lawyers have similar values.
Criminal defence lawyers defend persons accused of crime. We do not, for the most part, discriminate from one case to the next; for properly defending anybody accused by the State is critical to holding the government accountable in a free and democratic society. Our treatment of person's accused of crime also says a lot about the society we live in. That criminal lawyers defend accused, however, does not mean that we endorse the commission of criminal offences or wish-ill on anybody. Though by the very nature of our job we might appear to be the enemy of real victims, we are not.
With this in mind, I think I speak for most criminal defence lawyers when I say that it is not lost on us that while there are innocent accused people, there are also real criminals and real victims. It is our susceptibility to real criminals in this time of crisis that is the topic of this post.
A TARGET RICH ENVIRONMENT
Several media outlets have recently reported that fraudsters have been more active during the COVID-19 pandemic. To be sure, COVID-19 has created a target rich environment for the opportunistic.
I think I speak for most of us when I say that anybody who preys upon Canadians in this time of crisis is nothing more than the worst kind of contemptible reprobate. Though as a criminal defence lawyer, I would do my job and defend these people to the best of my ability – I am not insensitive to the carnage they cause.
To date, the coronavirus pandemic has swept across Canada. It has infected thousands of Canadians and killed hundreds. The world tally presently sits a nearly 1.3 million people infected with greater than 70,000 dead. These numbers are growing exponentially with each passing day.
https://www.worldometers.info/coronavirus/
Beyond the number of infected and the death toll, people across the planet are coping with a myriad of added stress, to include financial hardship, physical deterioration and emotional suffering. Unfortunately, for some Canadians, add to this the stress of being the victim of fraud.
According to the Government of Canada, scammers have been increasingly active. They have been phishing for personal information.
The Canadian Anti-Fraud Centre has identified a number of COVID-19 related fraud schemes:
- Cleaning or heating companies offering duct cleaning services or filters to protect from COVID-19.
- Local and provincial hydro/electrical power companies threatening to disconnect services for non-payment.
- Centers for Disease Control and Prevention (CDC) and/or the World Health Organization (WHO) offering fake lists for sale of COVID-19 infected people.
- Public Health Agency of Canada giving false results asserting the target has tested positive for coronavirus. The con-artist then asks for health card and credit card information for the purpose of a prescription.
- Red Cross and other known charities offering free medical products (e.g. masks) for a donation.
- Government departments sending out coronavirus-themed phishing emails tricking targets into opening malicious attachments programmed to capture sensitive personal and/or financial details.
- Financial advisers pressuring people to invest in hot new stocks related to the disease.
- Offers of financial aid and/or loans to assist in this time of crisis.
- Door-to-door salespersons selling household decontamination services.
- Private companies offering fake COVID-19 tests for sale.
https://www.antifraudcentre-centreantifraude.ca/features-vedette/2020/covid-19-eng.htm
Recently, Global News released a story titled “Scammers have never had a more target rich environment amid [the] coronavirus pandemic”. As written, “[t]he coronavirus pandemic has created a perfect storm for scammers seeking to defraud panicked, isolated and emotionally vulnerable targets”.
https://globalnews.ca/news/6741981/coronavirus-covid-19-scams/
While all of us are susceptible to fraud when things are stable, our vulnerability increases dramatically in a time of crisis. When we are panicked, isolated or emotionally vulnerable the risk of making poor decisions or snap judgments increases. This vulnerability does not only exist at the point of direct personal contact with fraudsters datamining our personal information, it exists with the many legitimate third-party custodians of our personal information – to include businesses such as telephone companies, financial institutions and a host of other organizations (including the Government) who possess or have access to our personal data. As reported by Global in 2018, the Canada Revenue Agency may have breached the privacy of thousands of Canadians.
"The personal, confidential information of over 80,000 individual Canadians held by the Canada Revenue Agency may have been accessed without authorization".
https://globalnews.ca/news/4273925/cra-privacy-breaches-searches-documents/
In my opinion, the security of our personal information held by legitimate third parties is only as good as the security protocols in place to protect that information. Furthermore, those same protocols are only as good as the people tasked with enforcing and adhering to them. In other words, flimsy security protocols put our information at risk just as readily as flimsy people.
THE PORTING SCAM
An example of a fraud involving flimsy protocols and flimsy people is the porting scam.
The “porting scam” is one where fraudsters exploit gaping cracks in business and security protocols at Telcos (such as Bell Mobility, Telus and Rogers Communications) for the purpose of ultimately thwarting online security at banks. The porting scam is done to steal the target’s mobile telephone number and then utilizing that stolen number to gain access to the target’s banking information. This scam has been prolific in Canada since at least September 2019.
https://bc.ctvnews.ca/cellphone-industry-leaves-canadians-vulnerable-to-identity-theft-1.4576801
This Calgary criminal lawyer fears that with long COVID-19 related waiting times at customer service call centres for all businesses (including telephone companies and banks), fraudsters may have even a greater opportunity to pull off a bank account heist.
The rip-off begins with the target’s mobile telephone number being surreptitiously ported to a different carrier company. This is accomplished when the fraudster attends a local Mobility outlet posing as the target, signs a new mobile telephone contract in the target's name and triggers the porting of the target's telephone number to the new carrier (such as from Bell to Telus). To achieve this, all a scammer needs to do is intercept a piece of mail (such as a telephone bill) and perhaps have at their disposal a few other pieces of innocuous information (such as an email address or other data collected from social media) to pose as the target and there is a good possibility that a salesman at the local mobility outlet will happily sign-up a new contract and trigger a transfer
In many cases, once the fraudster gains control over the target’s mobile telephone number, they are able to use the fraudulently ported number to exploit weaknesses at the customer service level of the target’s financial institution (to include Canada’s big banks). This is done by using the telephone number to trigger a full security measures reset of the target's online banking protocols, with new passcodes messaged to the victim’s telephone number on file (often a cellphone number now in the possession of the fraudster).
Once security measures have been reset and a new passcode sent to the stolen number, the fraudster has the keys to the kingdom. With these keys, the fraudster gains unfettered access to the victim’s online banking services, including his or her bank account. While the target either doesn’t realize his or her mobile signal has disappeared or is trying to figure out why there is no service, the fraudster is robbing money and other personal information from the illegally accessed bank account.
All of Canada’s mobile carriers and financial institutions are aware of this scam. From reading this post, you are now aware of it too.
security MEASURES EXPLOITABLE
What is frightening about this swindle is that the target/victim often did little or nothing to facilitate the fraud.
We often think that thieves must have hacked-into our computer when in reality, they only had to hack human frailty at the third-party/business level.
In the view of this Calgary criminal lawyer, though most institutions have carefully crafted privacy protocols, those measures are only as good as the people tasked with enforcing them.
Ask yourself how many times you have called a company for legitimate personal reasons, forgot a security question or password, only to have the customer service agent ask a series of soft questions to confirm identity.
For instance, just a couple of weeks ago, I spoke with an agent at Shaw Business Solutions about updating my credit card information. I needed to update my payment information because about a month prior, I was the victim of a fraud that resulted in my then credit card having to be replaced. The customer service agent asked questions to confirm my identity, to include querying about the last “4 digits” of the credit card number on file.
Frankly, I found this question disturbing because I just informed the customer service agent at Shaw that my credit card was replaced because I was the victim of fraud; meaning that she asked a question to confirm identity that was obviously information potentially in the hands of a con-artist. I couldn’t help but think, “what a stupid question”.
Of course, I no longer had that credit card (for it had been previously destroyed), and thus I had no idea (unlike the fraudster who might still be in possession of it) what the last 4 digits were. I had to persuade the customer service agent to ask me something else to confirm my identity.
Now, just for the moment, lets evaluate the strength of a security question asking about the last 4 digits on a credit card. Isn’t this question so soft as to be virtually useless? After all, the last 4-digits of a credit card number appears on many paper receipts and bills that just about any shaky-handed rogue could easily intercept from a trashcan, the drawer of a cash register or through the mail.
This left me to ponder how easy it is for fraudsters to exploit third-party institutions for a fraudulent purpose. I think the answer is “often”.
In my opinion, the success rate for many frauds is probably little more a numbers game. Though fraudsters will fail the vast majority of the time, every so often, they succeed. Call enough times and you might find an unsuspecting rube prepared to surrender his or her social insurance number or credit information. Be persistent enough and you might find an apathetic or untrained salesman or customer service agent who is prepared to soften security protocols just to complete a sale or move-on to the next caller. Worse, as the incentives for committing fraud seem to be significant enough to justify the risk, we cannot ignore the likelihood that many scams are perpetrated or assisted by insiders. An “insider” is somebody at the organizational level who may be privy to information unavailable to others; perhaps even be a person who has easy access to sensitive personal or financial details.
COVID-19: An Asset for Fraudsters
The coronavirus pandemic is a valuable asset for opportunistic fraudsters. As the chairman of TD Bank, Frank McKenna warned: “[t]his target-rich environment is compounded because the world is awash in promises of stimulus spending and financial assistance…”.
https://globalnews.ca/news/6741981/coronavirus-covid-19-scams/
With the promises of stimulus spending and financial assistance there is also an extreme lack of clarity as to how Canadians will access this relief. As we attempt to navigate the Internet to find information about how we access financial help, we might wonder, what websites can we safely visit, who can we safely talk to and what information can we safely reveal? These are all valid questions.
A word of warning: there have been many chameleon websites that have sprung-up to entice Canadians to enter and reveal personal and/or financial information. To diminish the likelihood of falling prey to this scam while you are searching for COVID-19 relief information, I encourage you to make every effort to confine your searches to known online entities, such as the actual Government of Canada website. I have included it here for your reference:
https://www.canada.ca/en/services/benefits/ei/cerb-application.html
Since many of us have retreated to home as part of a national effort to stop the spread of COVID-19, I encourage everybody to take the time to audit their own personal security. This includes contacting your Telco for the purpose of placing “port protection” on your mobile telephone number (an option Telcos should include free of charge anyway). Additionally, it's a good idea to review all passwords, for all online accounts, for the purpose of ensuring limited or no overlap from one account to the next. Evaluate the password strength and introduce or update all personal verification questions. While stuck at home, it's a good time to clean hard drives, assess your online behaviour and to be sceptical about every third-party telephone call that you receive. Be extra vigilant about websites you visit and be super-cautious about providing any personal information over the telephone, even to confirm it.
There are many steps all of us can do to protect ourselves. As a Calgary criminal lawyer who has defended many fraud cases over the years (and have even been the victim of fraud myself), I have a good understanding as to how frauds work. Therefore, if you have any questions, please do not hesitate to contact me to discuss your security. I won't ask you any personal questions; I might, however, be able to offer from experience some valuable insight so that you can protect yourself. This is a service that I am currently offering free of charge.
Be vigilant. Stay healthy.
David G. Chow
P.s.: attempted fraud since this post
Since writing the aforementioned post, a fraudster, phishing for information, targeted me with an email phishing scam.
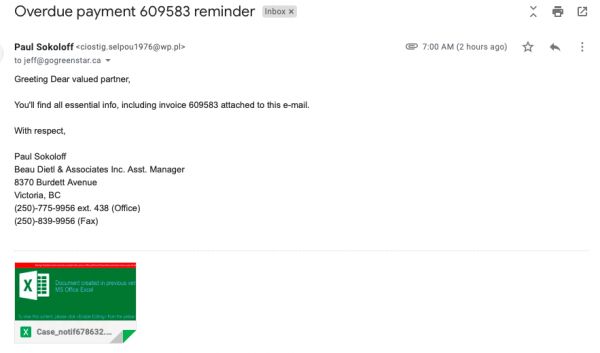
This is an example of a combination phishing and attempted theft. The scam works like this, the fraudster makes a demand to business for an unpaid bill. Likely the scammer is hoping the email lands on the desk of a shaky administrator, inattentive business owner or staff at the business that will just assume the legitimacy of the invoice and pay it. By paying the invoice, the scammer gets money and personal information.
Without going into all the details about how to identify the legitimacy of this fraudulent email, it is sufficient to say that the telephone number "(250) 775-9956" is "out of service".
I highlight this scam for my readers so that you don't fall for it.
Again, be vigilant.
p.p.s.: another attempted Fraud
On April 23rd, 2020 fraudsters targeted me again with an "Application for Employment" scam. The fraudster emailed under the pretext of applying for a job. The point of this scam is to entice the target to open an attachment containing "malware". The malware attachment could infect a computer (in particular, a desktop or laptop), by using Microsoft Word as the carrier for a contagion file. The phishing email looks like this:
Notice, the writer doesn't offer any insight in the email text about what job he/she is applying for. The email is very generic.
Additionally, it is important to be aware that the fraudster will use a name -- in this case Maria Rodriquez -- but when one looks at the email itself, it likely belongs to a different person. The email address used in this attempted fraud against me apparently belonged to a person named "Ben".
This is a very enticing fraud that any ordinary person (even one who is trying to be diligent), could fall prey by accident. When the attachment is opened, this is what you see (DO NOT OPEN THE ATTACHMENT AT ALL):
This is a malware file. This file likely contains a virus that will compromise a computer, potentially providing a means for information gathering by the fraudster. This phishing scam could provide a fraudster with tools to commit a bigger and more devastating fraud against the target.
Again. Be very careful. In my opinion, we are getting a point where we should not open any emails that we do not recognize.
David Chow
Calgary Criminal Lawyer | Calgary Fraud Lawyer
Calgary Criminal Defence Lawyer | Cochrane Criminal Lawyer | Full Service Alberta criminal lawyer
